Each player has their previous online sessions saved and can be viewed separately from their overall stats. SQL Injection results from failure of the application to appropriately validate input. An attacker leverages a weakness present in the database access layer code generated with an Object Relational Mapping ORM tool or a weakness in the way that a developer used a persistence framework to inject his or her own SQL commands to be executed against the underlying database. Kyle Katarn Saber HD. Lots of work went into the recoding and structure, too many to list here. 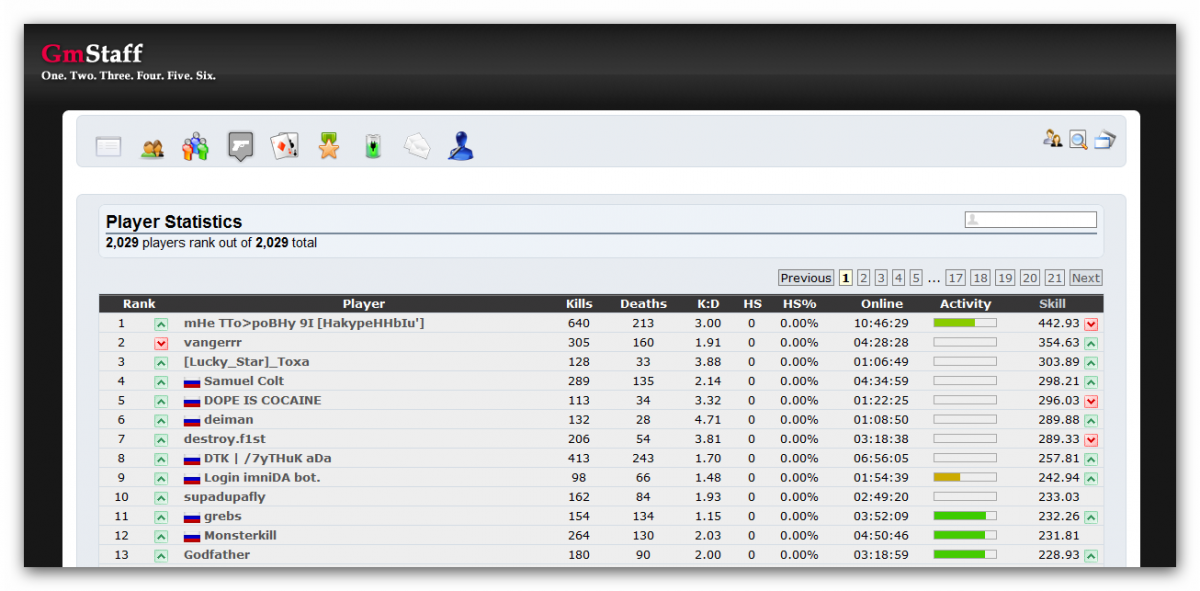
| Uploader: | Kigarr |
| Date Added: | 7 June 2017 |
| File Size: | 18.49 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 4212 |
| Price: | Free* [*Free Regsitration Required] |
SQL injection vulnerability in awards.
If the above pwychostats executes properly, then the attacker knows that the first character in a table name in the database is a letter between m and z. For example, the attacker can extract table names from a database using the following types of queries: The time now is Depending upon the database and the design of the application, it may also be possible to leverage injection to have the database execute system-related commands of the attackers' choice.
So psychoxtats the -daily command line manually is optional.
PsychoStats 3.2.2b Blind SQL Injection
Highest Rated FoxBot 0. This would psychostat some players to have slightly lower stats than what the logs actually reflect.
High quality fonts 1.
However, almost every data base management system DBMS system pdychostats facilities that if compromised allow an attacker complete access to the file system, operating system, and full access to the host running the database. Without the error messages that facilitate SQL Injection, the attacker constructs input strings that probe the target through simple Boolean SQL expressions.
In order to successfully inject SQL and retrieve information from a database, an attacker:. An attacker leverages a weakness present in the database access layer code generated with an Object Relational Mapping ORM tool or a weakness in the way that a developer used a persistence framework to inject his or her own SQL commands to be executed against the underlying database. The awards system uses a plugin architecture to allow for more complex awards.
SQL Injection enables an attacker to talk directly to the database, thus bypassing the application completely. The admin config editor is dynamic and very easy to use. Webapps exploit for php platform. If it doesn't, then the attacker knows that the character must be between a psyxhostats l assuming of course that table names only contain alphabetic characters.
In order to successfully inject SQL and retrieve information from a database, an attacker: Incorrectly saying mysql 4. 32.
Terms Privacy Security Contact Help http: Although suppressing database error messages are considered best practice, the suppression alone is not sufficient to prevent SQL Injection. Including detailed stats based on psyhostats roles.
PsychoStats v3.2.2b
Applied iteratively, the attacker determines how and where the target is vulnerable to SQL Injection. Ban players by steamid, IP or name. Original Trilogy Sabers 2 19th August Traditionally SQL injections attacks are viewed as a way to gain unauthorized read psychostata to the data stored in the database, modify the data in the database, delete the data, etc.
This will help search engines to properly index your stats pages. Successful injection can cause information disclosure as well as ability to add or modify data in the database. A 'session' is the length of time the player was logged in, even between map changes. Also added 'label' field. Sometime later, an unscrupulous backend application or could be part of the functionality of the same application fetches the injected data stored in the database and uses this data as command line arguments without performing proper validation.
Lots of work went into the recoding and structure, too many to list here.
PsychoStats b sql injection
Currently basic player action and weapon awards are present. Statistics Total Files Total Downloads If enabled, compiled stats are reduced when old stats are removed.
The attacker can determine if the syntax and structure of the injection was successful based on whether the query was executed or not.

No comments:
Post a Comment